I believe the issue could be here:
-A zone_vpn_input -j zone_vpn_src_ACCEPT
should be
-A zone_vpn_input -j zone_vpn_src_REJECT
Given the UI source zone forwarding for the openvpn zone is set to REJECT:
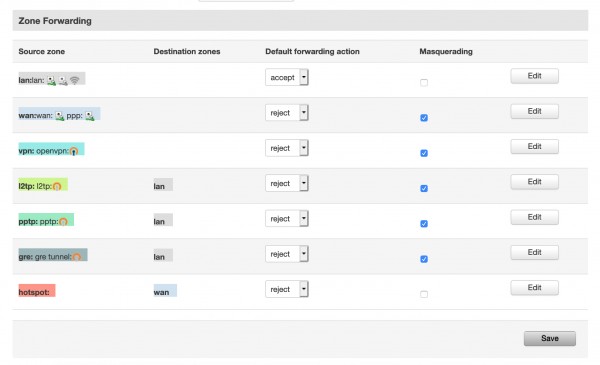
root@SYD_RUT950:~# iptables -S zone_vpn_input
-N zone_vpn_input
-A zone_vpn_input -m comment --comment "user chain for input" -j input_vpn_rule
-A zone_vpn_input -p tcp -m tcp --dport 80 -m comment --comment "Allow-VPN to RUT950 UI" -j ACCEPT
-A zone_vpn_input -p tcp -m tcp --dport 443 -m comment --comment "Allow-VPN to RUT950 UI" -j ACCEPT
-A zone_vpn_input -m conntrack --ctstate DNAT -m comment --comment "Accept port redirections" -j ACCEPT
-A zone_vpn_input -j zone_vpn_src_ACCEPT
root@SYD_RUT950:~# iptables -S zone_vpn_src_ACCEPT
-N zone_vpn_src_ACCEPT
-A zone_vpn_src_ACCEPT -i tun_+ -j ACCEPT
root@SYD_RUT950:~#