Dear,
I am unable to reach the teltonika and the LAN that the router openvpn client should act upon as gateway.
Openvpn allows for a client to act as gateway to for example: 192.168.44.0/24, now other openvpnclients from anywhere in the world can access devices behond the openvpnclient on the RUT 955.
See below:
172.27.232.1 (openvpn cloudserver)
172.27.3.44 (RUT 955) internal openvpn client address
192.168.44.168 (device in LAN of RUT 955 router)
In the .ovpn file a lot of information is included regarding the act as gateway functionality. Basically the client installed on the teltonika will act as gateway to other clients coonnected to the openvpn server to reach internal networks.
When I set this up on a RPI I have to add these iptable rules myself:
sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
sudo iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE
sudo iptables -A FORWARD -i eth0 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT
Furthermore I enable ipv4 forwarding = 1 in sysctl.conf
I assume the masquerading rules I enable in this window:
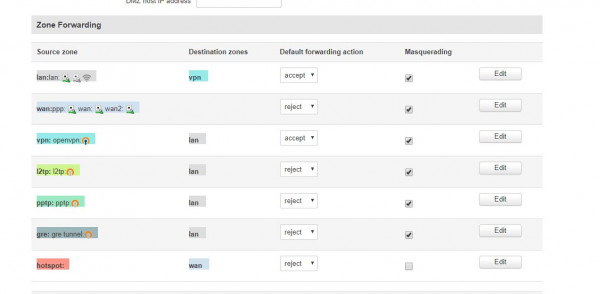
*note that I do this for vpn to lan but also another rule lan to vpn
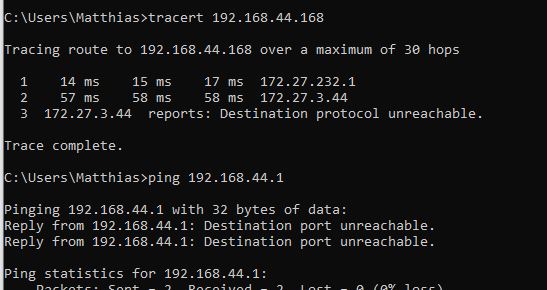
It did not work yet, So my tracert originating from my PC (open vpn client) knows to go to the openvpn server in the cloud and know to go to the openvpnclient on the teltonika but it gets refused there.
Now I am just adding more an more traffic rules:
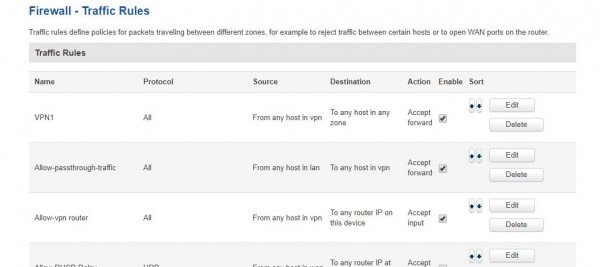
But still no luck. In summary
What does work:
client.ovpn file gets succesfully uploaded into teltonika + client connects succesfully to the server
traffic from the LAN behind teltonika can reach the VPN internal clients so lan->vpn traffic works
Where we are:
from another client(my pc) the tracert reaches the teltonika but teltonika refuses the incoming request.
vpn -> LAN traffic gets refused @ router
Thank you very much, we are btw very happy with teltonika products !
Matthias