I have same problem RUTX11 FW: RUTX_R_00.02.03
VPN Server: Synology Diskstation,
- Sat Feb 6 11:34:35 2021 daemon.err openvpn(Synology)[2002]: Certificate does not have key usage extension
- Sat Feb 6 11:34:35 2021 daemon.notice openvpn(Synology)[2002]: VERIFY KU ERROR
- Sat Feb 6 11:34:35 2021 daemon.err openvpn(Synology)[2002]: OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
- Sat Feb 6 11:34:35 2021 daemon.err openvpn(Synology)[2002]: TLS_ERROR: BIO read tls_read_plaintext error
- Sat Feb 6 11:34:35 2021 daemon.err openvpn(Synology)[2002]: TLS Error: TLS object -> incoming plaintext read error
- Sat Feb 6 11:34:35 2021 daemon.err openvpn(Synology)[2002]: TLS Error: TLS handshake failed
My setup looks like this:
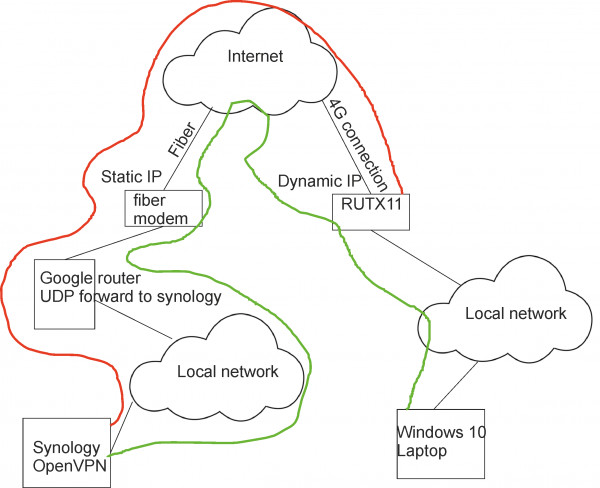
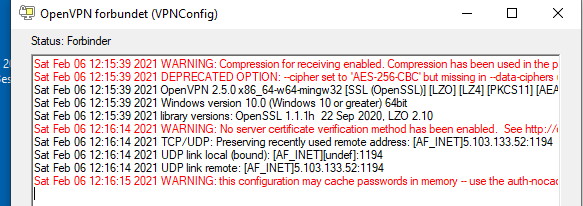
The funny part is I can get a PC to connect thru the RUTX11 (Green line) where I cannot get the RUTX11 to work (Red line), the windows 10 laptop is running openvpn version:
My RUTX11 setup is:
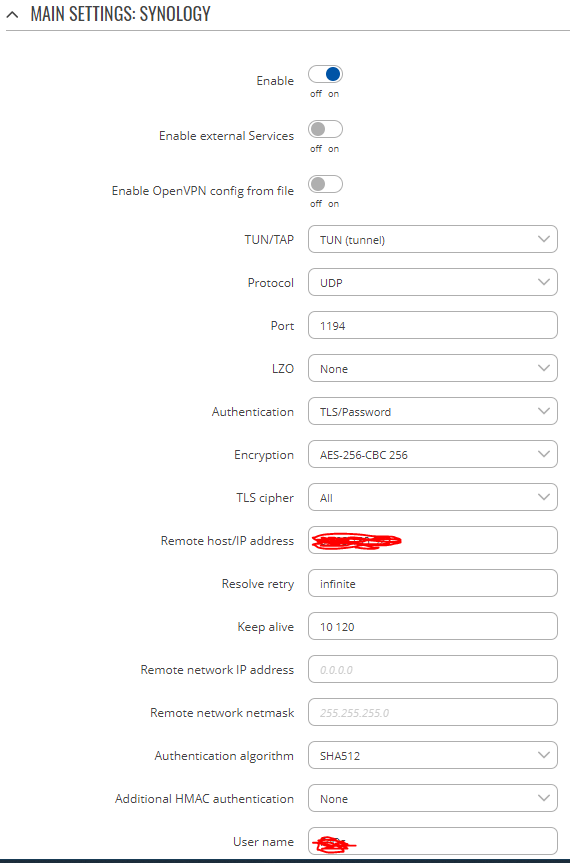
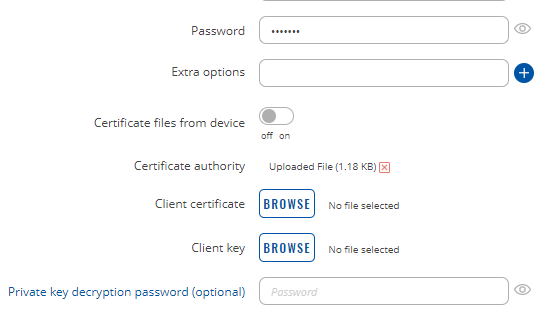
where Remote IP is the static IP, and username and password is the profile on synology, what has a output setup as this:
dev tun
tls-client
remote YOUR_SERVER_IP 1194
# The "float" tells OpenVPN to accept authenticated packets from any address,
# not only the address which was specified in the --remote option.
# This is useful when you are connecting to a peer which holds a dynamic address
# such as a dial-in user or DHCP client.
# (Please refer to the manual of OpenVPN for more information.)
#float
# If redirect-gateway is enabled, the client will redirect it's
# default network gateway through the VPN.
# It means the VPN connection will firstly connect to the VPN Server
# and then to the internet.
# (Please refer to the manual of OpenVPN for more information.)
#redirect-gateway def1
# dhcp-option DNS: To set primary domain name server address.
# Repeat this option to set secondary DNS server addresses.
#dhcp-option DNS DNS_IP_ADDRESS
pull
# If you want to connect by Server's IPv6 address, you should use
# "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode
proto udp
script-security 2
comp-lzo
reneg-sec 0
cipher AES-256-CBC
auth RSA-SHA512
auth-user-pass
<ca>
Any good ideas???