RUT950 : LAN 192.168.0.0/24
Remote ip endpoint = public ip pfsense interface
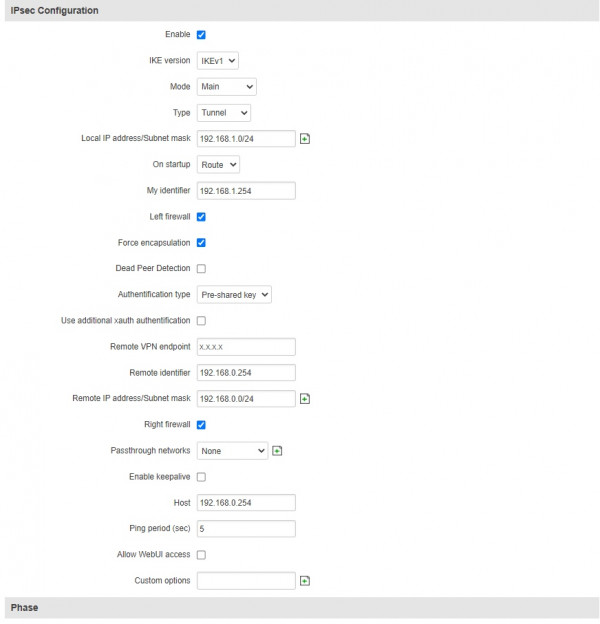
Pfsense: LAN 192.168.0.0/24
Remote gateway= 0.0.0.0 if RUT behind NAT otherwise public ip of RUT950
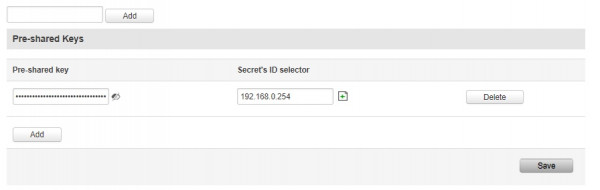
pre-shared-key=same on RUT, invent a key
nat_traversal="force" if RUT behind NAT otherwise "auto"
<phase1>
<ikeid>2</ikeid>
<iketype>ikev1</iketype>
<mode>main</mode>
<interface>wan</interface>
<remote-gateway>0.0.0.0</remote-gateway>
<protocol>inet</protocol>
<myid_type>address</myid_type>
<myid_data>192.168.0.254</myid_data>
<peerid_type>address</peerid_type>
<peerid_data>192.168.1.254</peerid_data>
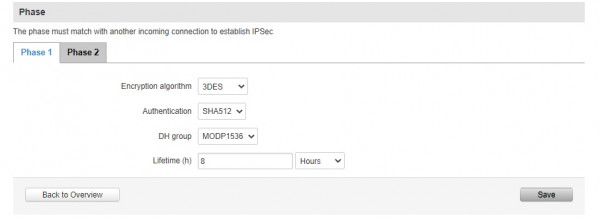
<encryption>
<item>
<encryption-algorithm>
<name>3des</name>
<keylen></keylen>
</encryption-algorithm>
<hash-algorithm>sha512</hash-algorithm>
<prf-algorithm>md5</prf-algorithm>
<dhgroup>5</dhgroup>
</item>
</encryption>
<lifetime>28800</lifetime>
<rekey_time></rekey_time>
<reauth_time>0</reauth_time>
<rand_time>0</rand_time>
<pre-shared-key>xxxx</pre-shared-key>
<private-key></private-key>
<certref></certref>
<pkcs11certref></pkcs11certref>
<pkcs11pin></pkcs11pin>
<caref></caref>
<authentication_method>pre_shared_key</authentication_method>
<nat_traversal>force</nat_traversal>
<mobike>on</mobike>
<closeaction>trap</closeaction>
<responderonly></responderonly>
<splitconn></splitconn>
</phase1>
<phase2>
<ikeid>2</ikeid>
<uniqid>7a4d58a6e595a</uniqid>
<mode>tunnel</mode>
<reqid>2</reqid>
<localid>
<type>network</type>
<address>192.168.0.0</address>
<netbits>24</netbits>
</localid>
<remoteid>
<type>network</type>
<address>192.168.1.0</address>
<netbits>24</netbits>
</remoteid>
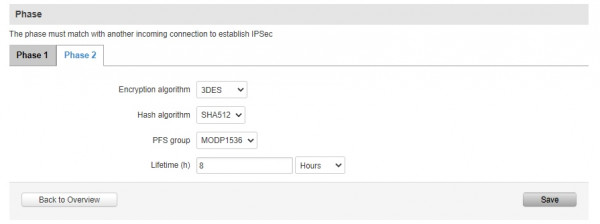
<protocol>esp</protocol>
<encryption-algorithm-option>
<name>3des</name>
</encryption-algorithm-option>
<hash-algorithm-option>hmac_sha512</hash-algorithm-option>
<pfsgroup>5</pfsgroup>
<lifetime>3600</lifetime>
<rekey_time>0</rekey_time>
<rand_time>0</rand_time>
<pinghost></pinghost>
</phase2>