Hi, couldn't reproduce your issue. Created a new zone, added an interface to the zone. 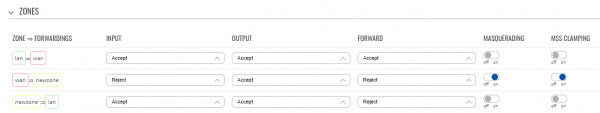
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
input_rule all -- anywhere anywhere /* !fw3: Custom input rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
syn_flood tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN /* !fw3 */
zone_lan_input all -- anywhere anywhere /* !fw3 */
zone_wan_input all -- anywhere anywhere /* !fw3 */
zone_newzone_input all -- anywhere anywhere /* !fw3 */
reject all -- anywhere anywhere /* !fw3 */
Chain FORWARD (policy DROP)
target prot opt source destination
forwarding_rule all -- anywhere anywhere /* !fw3: Custom forwarding rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_forward all -- anywhere anywhere /* !fw3 */
zone_wan_forward all -- anywhere anywhere /* !fw3 */
zone_newzone_forward all -- anywhere anywhere /* !fw3 */
reject all -- anywhere anywhere /* !fw3 */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
output_rule all -- anywhere anywhere /* !fw3: Custom output rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_output all -- anywhere anywhere /* !fw3 */
zone_wan_output all -- anywhere anywhere /* !fw3 */
zone_newzone_output all -- anywhere anywhere /* !fw3 */