I think I finally crafted and found solution to my own ticket that resolves the case, by myself.
Below you can find full description and explanation. However, this should be also addressed and fixed somehow globally by Teltonika Development guys in next RutOS versions.
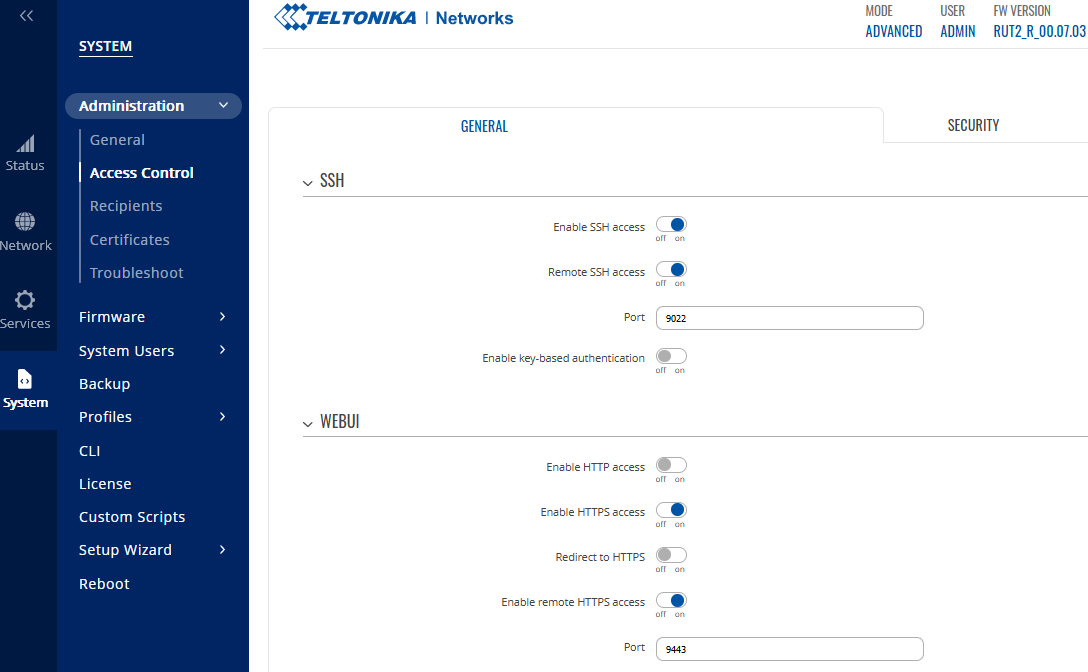
First of all, once you enable in RutOS Remote Management options -> System -> Administration -> Access Control [General] that involves use of SSH/HTTP/HTTPS like:
- Remote SSH access over port 22 (my example 9022)
- Enable remote HTTP access over port 80
- Enable remote HTTPS access over port 443 (my example 9443)
Teltonika RUT240 device (I guess other devices too) should create specific rules that allows such traffic to be handled by device itself. You should find these rules exactly in Firewall -> Port Forwards section.
When RUT240 works in normal NAT mode for Mobile interface -> all sections of Firewall are operating and taking care of the traffic, like: General Settings / Port Forwards / Traffic Rules / NAT Rules.
When RUT240 works strictly in Passthrough mode for Mobile interface (changed from default: NAT mode) -> only Firewall->Port Forwards section is the matter for us and other sections are skipped and not used for analyzing traffic, anymore. This is how IP traffic is passing through to other device connected behind Teltonika.
That’s why, even when you have still set and active rules allowing specific IP traffic in configuration,
they will not work any longer in practice (for example, you can check out e.g: Traffic Rules subtab in Firewall).
These kind of rules works when the router is set to NAT mode only, in other modes they do not apply.
Unfortunately, current firmware version 07.03 of RUT240 doesn't directly inform the user that he must additionally configure these rules manually, for remote management to work.
I wish Teltonika RUT240 should also additionally inform us too with some information message,
when changing operating mode from NAT to Passthrough and saving settings about it, like:
“ATTENTION! Changing operating mode from NAT to Passthrough actually disables analysis of forwarded IP network traffic, including most of built-in firewall rules. For other traffic to be handled and destined to Teltonika make sure to configure such rules manually in Port Forwards section, if needed.” -> this could be informative for standard user that he also needs to perform some actions to something to work.
Generally, I think it should doesn't matter you in what order you configure sections, as final result you should be able to have device set as Passthrough and full Remote Management to it, so it can be either way configured:
first set Passthrough <> then set Remote Management options
or vice-versa
first set Remote Management options <> then set Passthrough
From perspective of different firmware versions this looks as follows:
* Legacy RutOS firmware RUT2XX_R_00.01.14.6 didn’t have any problem with set Passthrough mode + automatically create additional set of Port Forwards rules, so everything was working out of the box.
User didn’t need to care about it, because everything was working, by default.
Once you reconfigured RUT240 device you could see its effect and in running, when navigating to:
Network -> Firewall -> Port Forwarding, where we see our intended rules for remote management.
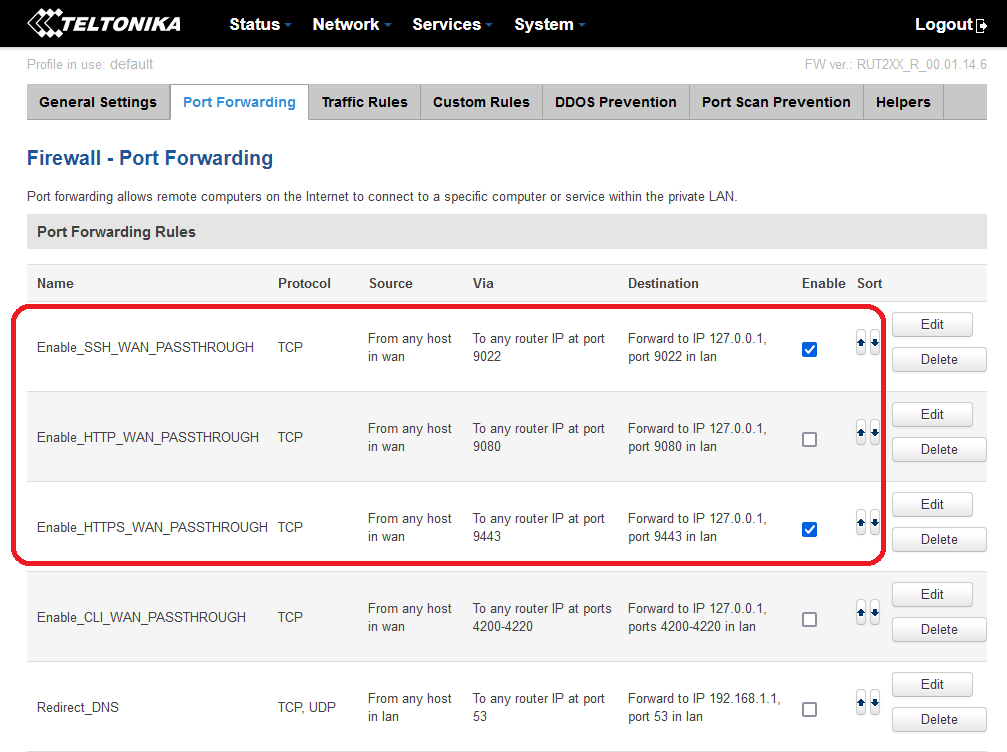
Rules on the list:
- Enable_SSH_WAN_PASSTHROUGH
- Enable_HTTP_WAN_PASSTHROUGH
- Enable_HTTPS_WAN_PASSTHROUGH
Clearly, rules says what they are intended and supposed to do [based on my Example for HTTPS]:
“Traffic from any source from Internet destined to port TCP HTTPS 9443 is forwarded (redirected) and handled by router-itself/RUT240/, meaning its internal interface as 127.0.0.1, which is Loopback interface“
This makes sense to me. It's logical and understandable. Same thing happens for HTTP and SSH.
Remember: here its internal operating interface for working rule is interface Loopback – 127.0.0.1.
We can see this rule details by clicking Edit:
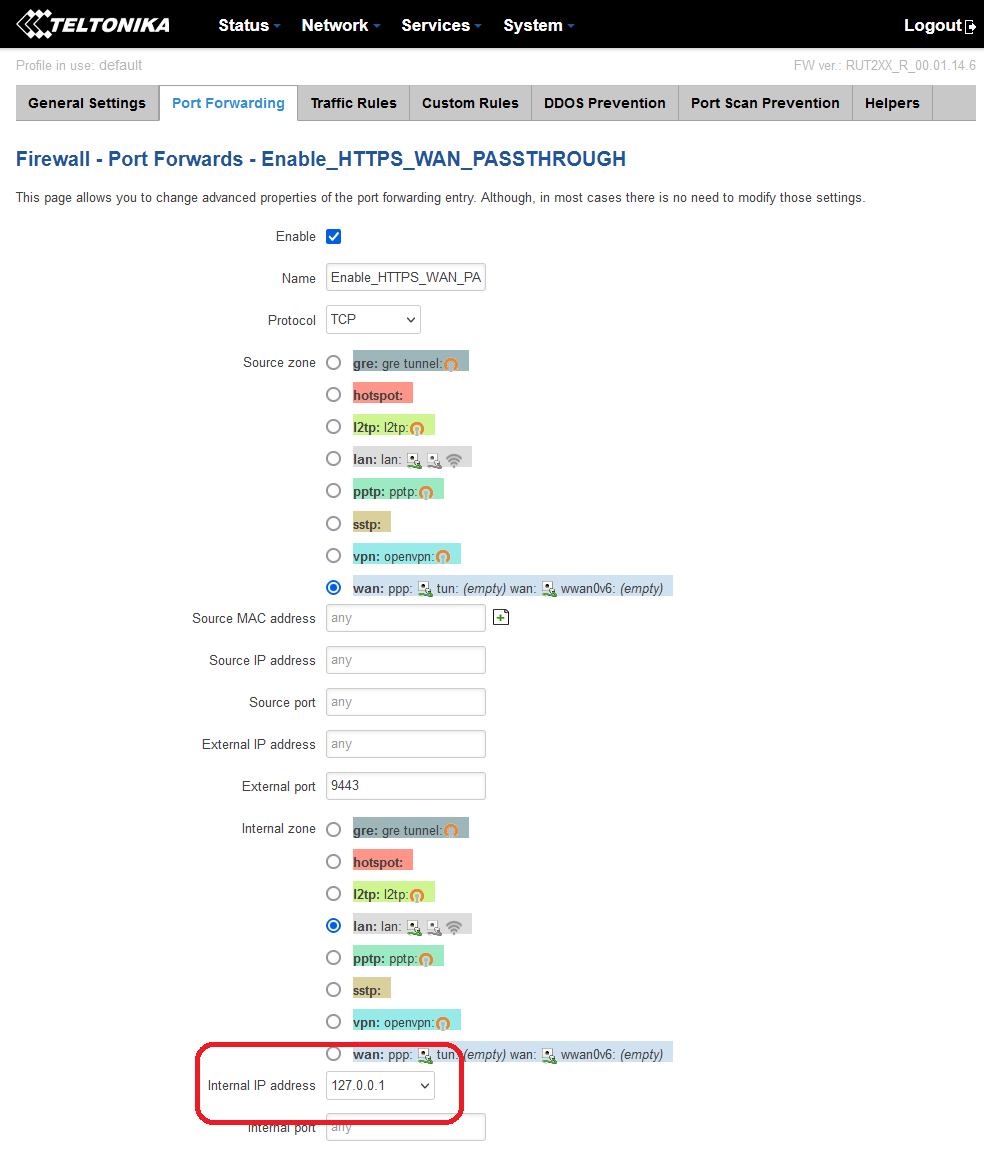
Moving on to next scenario *Migration from Legacy 14.6 RutOS firmware into first RUT2_R_00.07.01.2:
Upgrading from Legacy RUT2XX_R_00.01.14.6 with keeping settings into very first RUT2_R_00.07.01.2.
Here, it looks like rules has been imported and recreated exactly in the same way, but in my case, remote management failed for HTTPS/SSH. Take a look at screen in Firewall -> Port Forwards section:
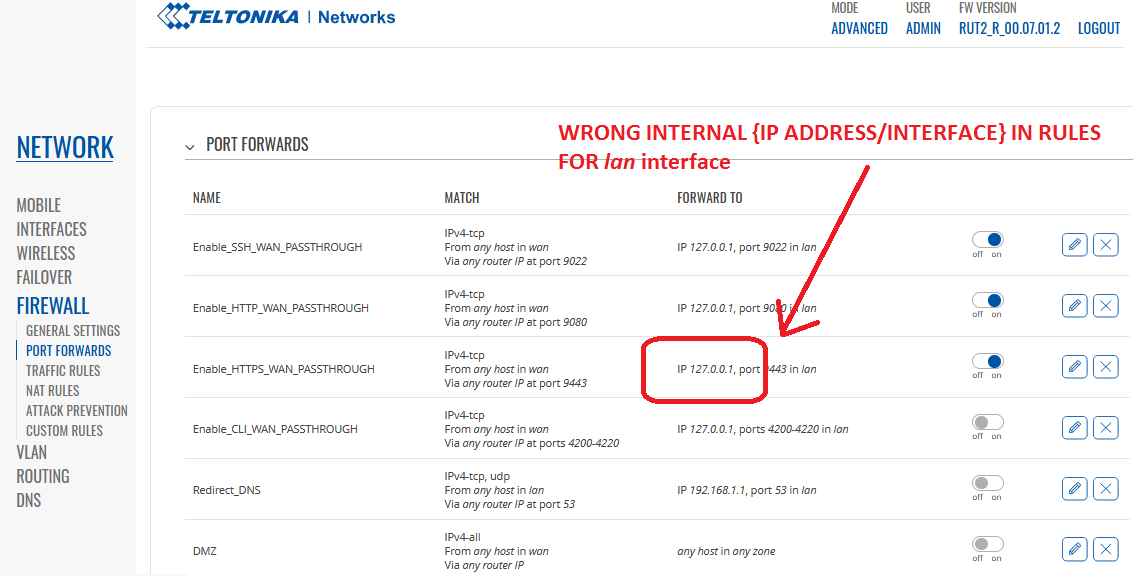
Here, example rule Enable_HTTPS_WAN_PASSTHROUGH, even that looks similarly as in Legacy firmware,
it’s no longer usable and not working correctly operational as it states. We will not have remote access. Why?
It’s because in newer firmware internal interface as Loopback – 127.0.0.1 is not applicable and recognized as valid interface for definition when creating and writing new Forwarding rules. It must be selected exactly the same as lan interface, specifically. So, now for new rules, to be created, we see that valid interfaces on the drop down list are as follows:
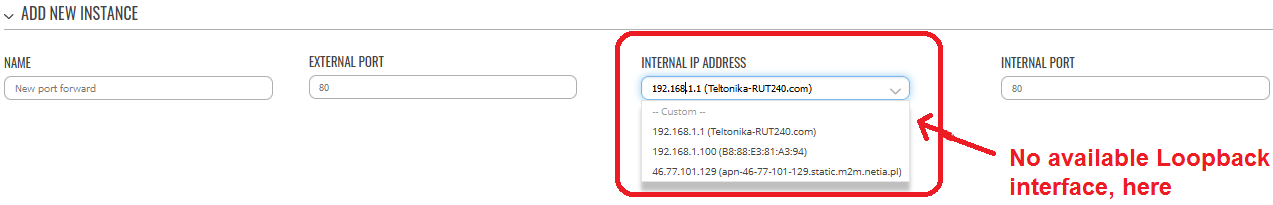
In fact, behind the scene, in RutOS we see that Loopback interface still exist, but it shouldn’t be no longer used in definition of the rules. Some other mechanisms works here. I dunno.
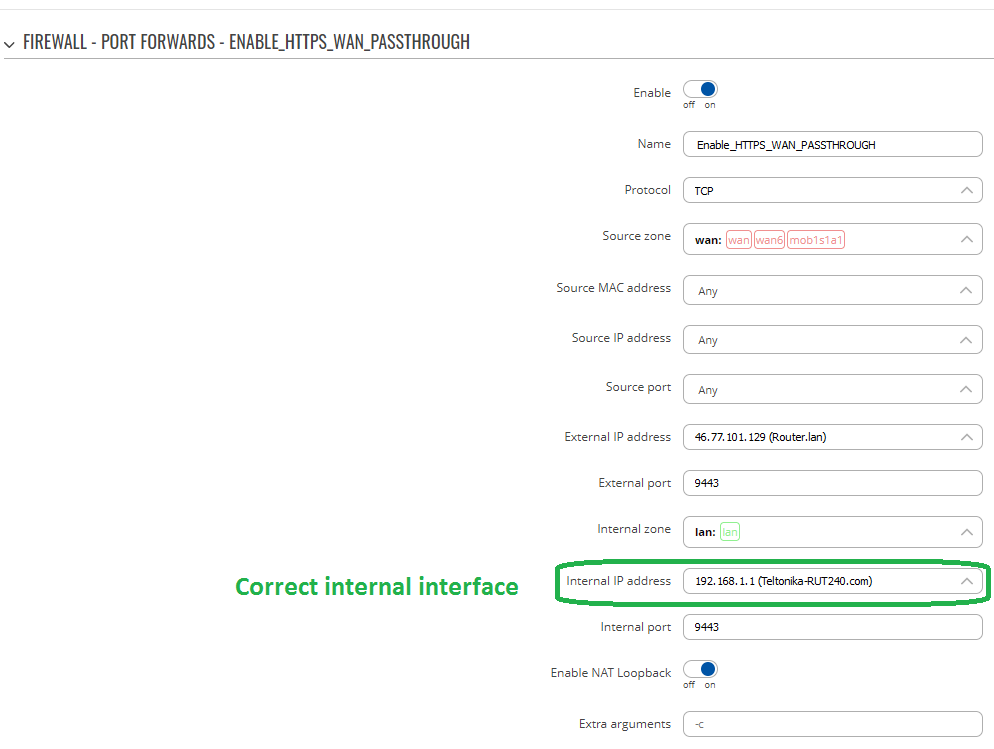
Overall, this is the Root Cause of Fault for missing HTTPS remote access - mismatching interface that should be changed from wrong 127.0.0.1 (Loopback) to correct 192.168.1.1 (Teltonika-RUT240.com) interface.
If you manually Edit specific rule on the Port Forwards list and set parameter “Internal IP address” and its value to: 192.168.1.1 (Teltonika-RUT240.com), you should restore full management access via HTTPS.
It looks like to me, while migrating settings from Legacy firmware RUT2XX_R_00.01.14.6 into RUT2_R_00.07.01.2,
software didn’t correct and mapped old configuration interface Loopback into new definition rule using lan interface (192.168.1.1 Teltonika-RUT24.com). This should be fixed, I guess in upcoming software releases.
Last case scenario using newest RutOS firmware, both: *RUT2_R_00.07.02 and RUT2_R_00.07.03:
when configuring everything from factory default settings, set Passthrough for Mobile interface mob1s1a1 and Remote Management options.
Whatever approach you choose, at the beginning, you end up with the same result, failed:
first set Passthrough <> then set Remote Management options or vice-versa
first set Remote Management options <> then set Passthrough
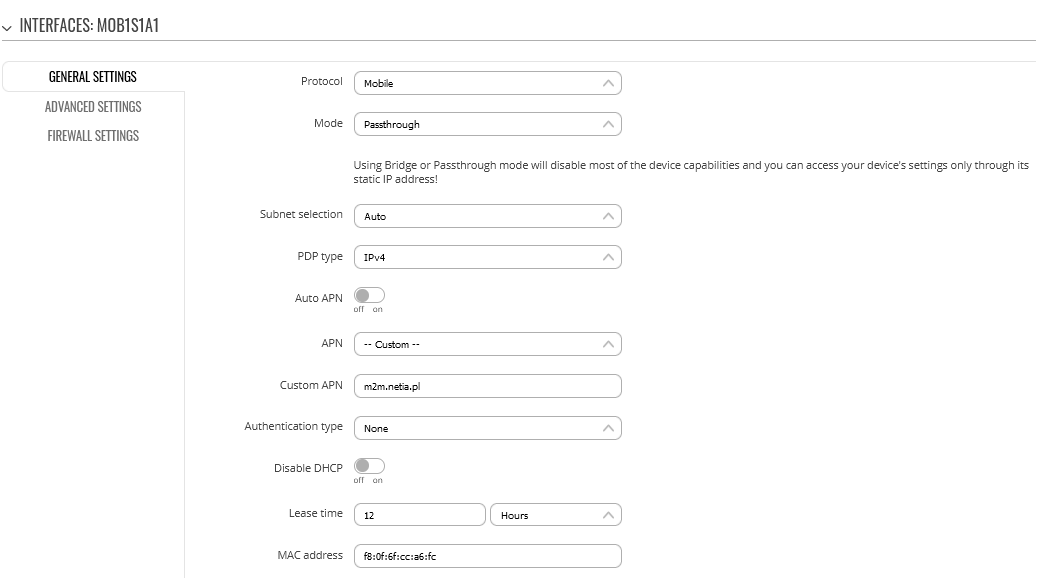
Going to Firewall -> Port Forwards section we see that list is completely empty, but firmware should by default add here automatically respective rules for remote HTTPS and SSH access (my Example port 9443 and 9022). Nothing is added by RutOS, sadly.
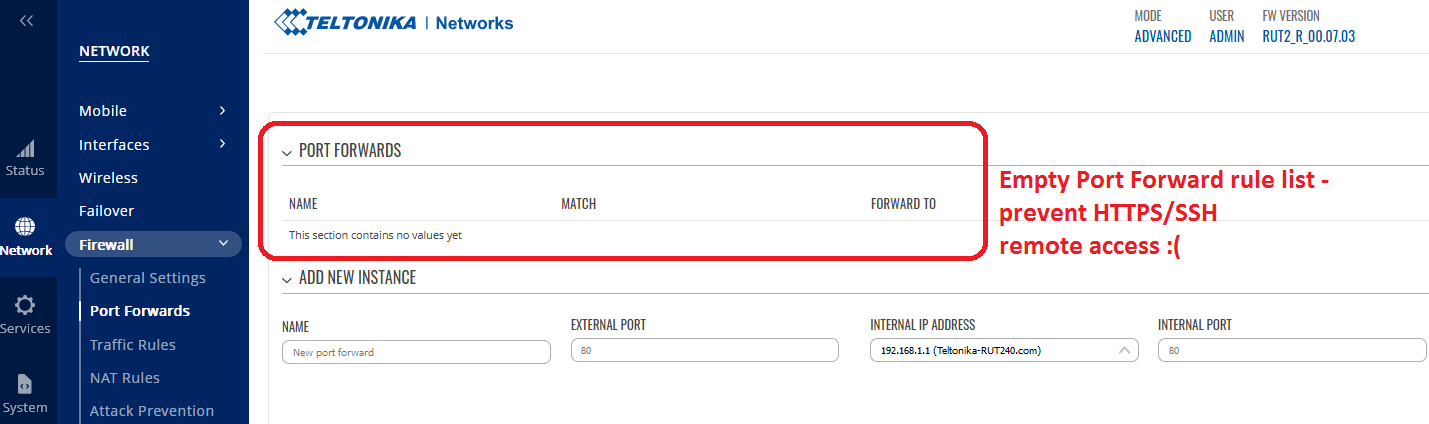
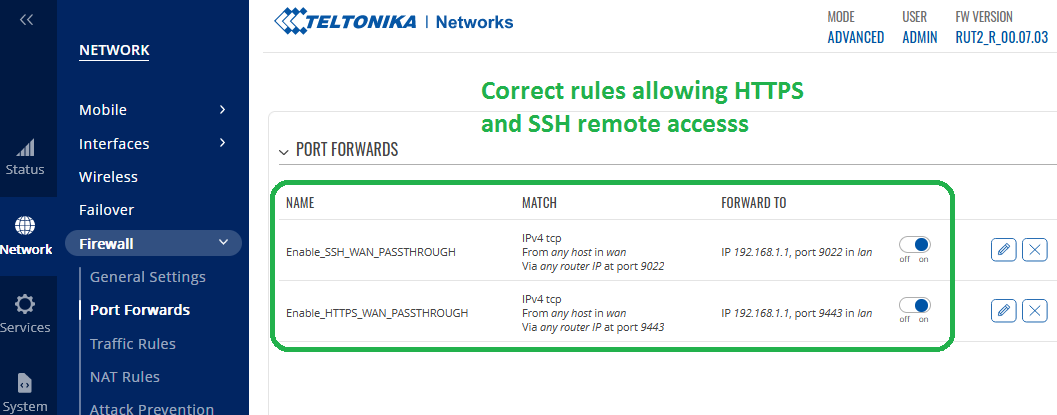
Now you need to manually create specific rules in order to have external remote access via HTTPS and SSH.
Rules will allow and enable incoming traffic for remote access via HTTPS 9443/SSH 9022 to be redirected (to be forwarded and terminated) at Teltonika, while rest remaining traffic for other ports to be passed through (transparently) to Cisco.
Interesting fact is that Interface 192.168.1.1 (Teltonika-RUT240.com) in rules points to port lan, this is only rule-mapping, so regardless of current status of physical port Up/Down – those rules will always cause redirecting traffic to internal interface at Teltonika 9443/9022.
We add here new rules by typing:
Name = Enable_SSH_WAN_PASSTHROUGH
External Port = 9022
Internal IP Address = 192.168.1.1 (Teltonika-RUT240.com) > choose from drop down list
Internal Port = 9022
Name = Enable_HTTPS_WAN_PASSTHROUGH
External Port = 9443
Internal IP Address = 192.168.1.1 (Teltonika-RUT240.com) > choose from drop down list
Internal Port = 9443
Click Add and then Save & Apply
Detailed configuration of policy HTTPS_WAN_PASSTHROUGH after clicking button Edit:
This should fix problems with remote access.