Hello,
This menu utilizes a Linux utility called NetStat.
Via the CLI you can access this data by running the command netstat -l
Currently in v7.4.x there seems to be an issue with this menu window, where some of the data is displayed incorrectly. It is supposed to look like this:
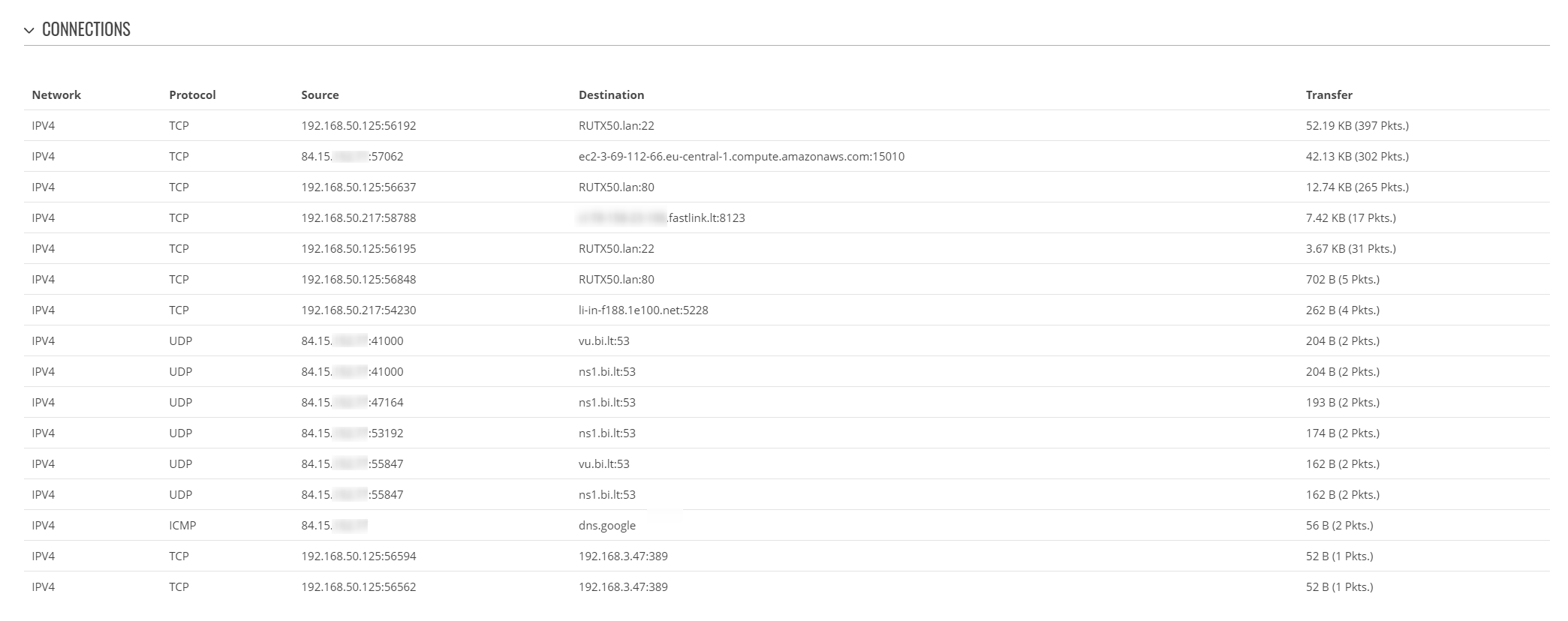
The blurred addresses (except the one on the right) are the WAN address of the device in question.
NetStat also has a few different arguments to differentiate the data source and the activity of the connection.
Let me know if any additional information is needed.
Best regards,
DaumantasG