Hello,
Instead changing general settings, try creating Traffic Rules in router's firewall, which should prevent reaching devices behind the router on certain ports, or router itself when connecting via certain interface.
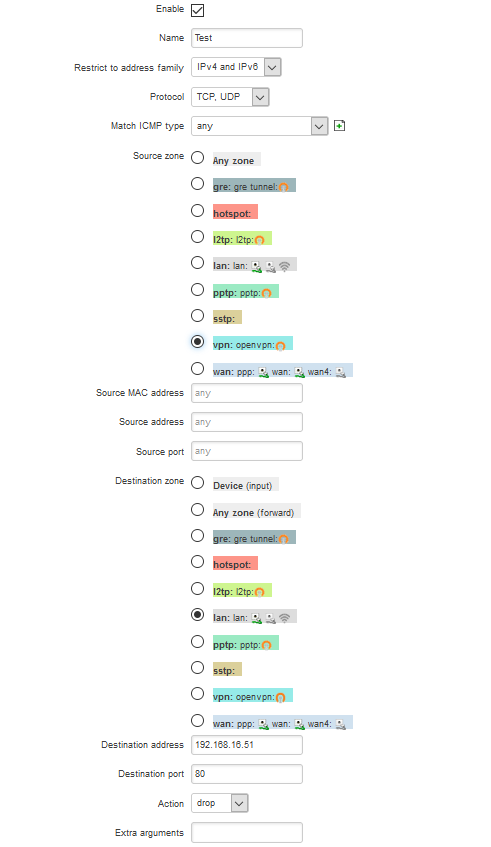
To create new rule, simply navigate to Traffic Rules submenu in Firewall menu and in New Forward Rule section create a traffic rule, by entering the name and selecting the interfaces:
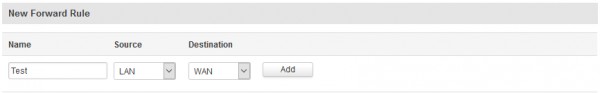
Once pressed "Add", you will be redirected to Traffic Rule configuration window, which allows to select more options, like protocol, port, IP and etc.
Here you can select rules to block traffic coming from OpenVPN interface to certain device's port.
E.g. to block ability to reach printer on http port from openvpn interface, the rule should look similar to below: