Hello! I hope you are all doing well and I want to see if someone can shed some light in this issue I'm having.
From the documentation, it isn't clear to me how to proceed that's why I decided to ask a question.
I have the following setup:
LAN (192.168.1.X/24) <-> RUT240 (192.168.1.9/24) (OpenVPN server 172.42.0.0/24) <-> Internet <-> OpenVPN client (172.42.0.6/24)
My desire is simple: I want to be able to ping 192.168.1.X/24 range from 172.42.0.X/24 range NATing in 192.168.1.9.
To clarify even more with an example: I want to ping 192.168.1.11 from 172.42.0.6; 192.168.1.11 must receive the ICMP request from 192.168.1.9, 192.168.1.9 will have the reply from 192.168.1.11 and answer back to 172.42.0.6. And old as hell simple NAT, but just to be clear in what I want :-D
After reading the RUT240 documentation it's still yet not clear to me how to do this.
Once I've setup my OpenVPN server and pushed 192.168.1.0 routes to clients (via client config) I thought I had to do nothing more since I saw the following info in the Zone Forwarding config:
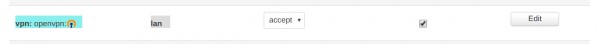
Which I understand as "all packets from OpenVPN interface going to LAN destination are forwarded with Masquerade (NAT)"
My general settings are:
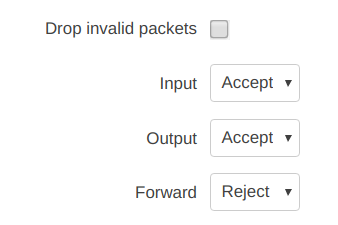
I SSH'ed into RUT240 and executed:
iptables -t nat -L -n
I had in the output:
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
postrouting_rule all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3: user chain for postrouting */
zone_lan_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_wan_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_wan_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_vpn_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_l2tp_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_l2tp_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_pptp_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_gre_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_hotspot_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_hotspot_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_hotspot_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_hotspot_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_sstp_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
zone_zero_postrouting all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
Chain zone_vpn_postrouting (1 references)
target prot opt source destination
postrouting_vpn_rule all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3: user chain for postrouting */
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* !fw3 */
With that in mind, shouldn't the RUT240 be making the desired NAT already? What's missing?
Many thanks in advance!!