Hi Tomas
Sorry about the lang response time – weekend and other work-stuff came in the way ;)
Just to confirm - you have a device (with some service running) behind a CGNAT/firewall/third-party router to which you cannot gain any access or have someone configure a port forward for you?
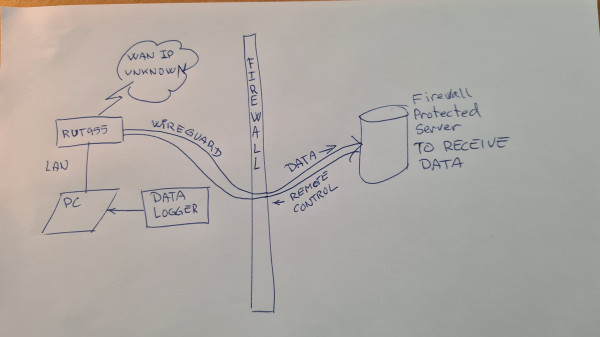
Not quite there yet. Goal is to be able to push data from the remote broadband installation, through our company firewall, even without knowing the remote BB WAN IP.
If that's the case then using a virtual private server (VPS) solution along with a WireGuard VPN tunnel to the end-device could be possible to do.
Q: Where is the VPS – a (paid) service from the Internet ?
In theory, by employing this method, you can create a tunnel between the RUT955 and the VPS.
The result of this - you can configure a working port forward through the WireGuard tunnel. The principle of this configuration (after setting it up) is the following:
<!--[if !supportLists]-->1. <!--[endif]-->Specify the public external VPS IP address and port to begin initiating connection from end-device A
I suppose ‘end device A’ will the server behind our firewall, and thus ‘end device B’ will be the RUT955-PC?
If so I believe that I want it the other way round – traffic initiates from remote to behind firewall.
<!--[if !supportLists]-->2. <!--[endif]-->The packet reaches VPS at specified port, VPS forwards this packet through the WireGuard tunnel to the RUT955
This I read as the VPS is our company firewall, on which there needs to be a rule, something like this:
<!--[if !supportLists]-->· <!--[endif]-->Allow incoming from ‘net’ on port ‘wireguard configured port#’ to firewall protected server (end-device B - ‘fps’)
<!--[if !supportLists]-->· <!--[endif]-->Handle key exchange between RUT955 and ‘fps’ to ensure validity
3. RUT955 processes this packet, forwards it to the end-device B (your Linux machine for example)
<!--[if !supportLists]-->4. <!--[endif]-->Packet from end-device B comes back the same way to your end-device A
If this is what you'd like to do then you may want to take a look at our Helium configuration example wiki page. It may not be designed precisely for your device/use-case but the principle of this configuration is the exact same - configuring a port forward to the end-device via WG tunnel when you cannot acquire a public IP address on your RUT955. Link to the article.
If this isn't what you'd like to do then please provide additional information and some details of how things should work from your end and, ideally, provide a topology of how things should be connected and work.
Best regards,
Tomas P.
I haven’t had the time to dig in to the article describing the Helium setup today, but I just wanted to get back to you with this for now.
Your help is highly appreciated, thanks!
Regards
Ole