thanks for response.
i followed that guides, and tunnel is up state. here is the IPSEC status:
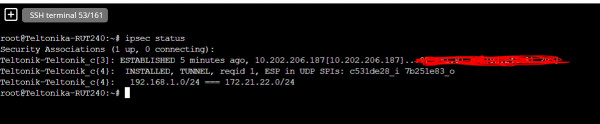
from 172.21.22.1 i can ping 192.168.1.1, but not in reverse direction.
traceroute fro teltonika shows that traffic is not inserted into ipsec tunnel :
traceroute to 172.21.22.1 (172.21.22.1) from 192.168.1.1, 30 hops max, 38 byte packets
1 * * *
2 10.231.219.33 (10.231.219.33) 43.163 ms 27.694 ms 21.395 ms
3 10.231.224.21 (10.231.224.21) 28.539 ms 23.795 ms 21.349 ms
4 host-213-157-192-222.customer.magticom.ge (213.157.192.222) 26.357 ms 29.601 ms 23.324 ms
5 host-213-157-192-213.customer.magticom.ge (213.157.192.213) 41.232 ms 26.412 ms 24.328 ms
6 host-213-157-192-49.customer.magticom.ge (213.157.192.49) 21.295 ms 34.187 ms 24.681 ms
7 84.44.20.157 (84.44.20.157) 45.259 ms 53.680 ms 49.217 ms
8 10.135.54.117 (10.135.54.117) 56.351 ms 55.825 ms 51.350 ms