Hi Andzej,
So as you asked here is a schema of what i want to achieve:
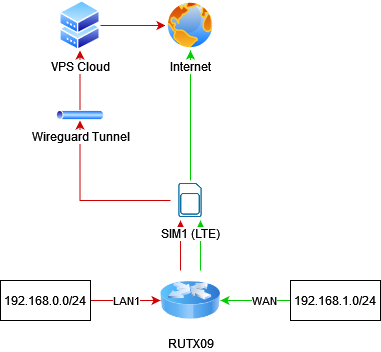
As you suggested i tried setting allowed ips to 0.0.0.0/1 and 128.0.0.0/1 but it didn't help.
I somehow managed to achieve what i wanted to by disabling the "Route allowed IPs" from the webui in the wireguard peer settings. By doing this everything started working as intended, at least until this morning.
Today i found that the tunnel wasn't working anymore and the devices on the 192.168.0.0/24 network could't connect to the internet obviusly (the vpn policy routes the traffic through the tunnel).
There was one more strange thing, i couldn't connect to the VPS either from both networks (cant ping the public ip address or connect with SSH) this IP is the remote server used in the wireguard peer configuration.
So the first thing i tried was rebooting both RUTX09 and the VPS, after that the wg command wasn't showing any handshake and the ping towards the VPS still wasn't working.
I tried to remove the gateway in the interface that i had to create in order to enable the vpn policy (WG_VPN), and the handshake was made. But the traffic wasn't being routed outside the VPN so i re-added the gateway, and things started working as yesterday.
If i reboot the device the problem persists and have to remove/add the gateway on the interface to make things work, its like the RUTX09 is trying to reach the public ip address of the vps through the tunnel, but the tunnel is not up yet, because it cant reach the ip through it?
Im gonna share my configuration so you have a clear view of what im doing:
- The created interface WG_VPN:
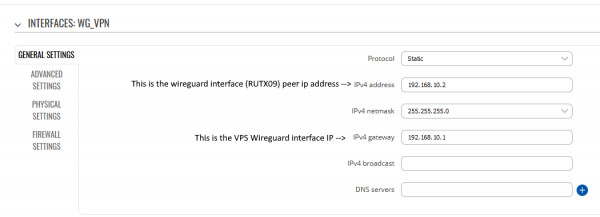
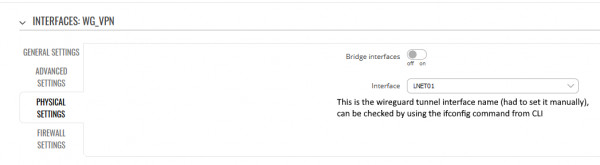
- Tunnel settings (keys censored):
The RUTX09 firmware version is RUTX_R_00.07.00.
And here is the "uci show vpn-policy-routing" output:
root@Teltonika-RUTX09:~# uci show vpn-policy-routing
vpn-policy-routing.config=vpn-policy-routing
vpn-policy-routing.config.verbosity='2'
vpn-policy-routing.config.strict_enforcement='1'
vpn-policy-routing.config.src_ipset='0'
vpn-policy-routing.config.dest_ipset='0'
vpn-policy-routing.config.resolver_ipset='dnsmasq.ipset'
vpn-policy-routing.config.ipv6_enabled='0'
vpn-policy-routing.config.ignored_interface='vpnserver wgserver'
vpn-policy-routing.config.boot_timeout='30'
vpn-policy-routing.config.iptables_rule_option='append'
vpn-policy-routing.config.procd_reload_delay='1'
vpn-policy-routing.config.webui_enable_column='0'
vpn-policy-routing.config.webui_protocol_column='0'
vpn-policy-routing.config.webui_chain_column='0'
vpn-policy-routing.config.webui_show_ignore_target='0'
vpn-policy-routing.config.webui_sorting='1'
vpn-policy-routing.config.webui_supported_protocol='tcp' 'udp' 'tcp udp' 'icmp' 'all'
vpn-policy-routing.config.enabled='1'
vpn-policy-routing.@include[0]=include
vpn-policy-routing.@include[0].path='/etc/vpn-policy-routing.netflix.user'
vpn-policy-routing.@include[0].enabled='0'
vpn-policy-routing.@include[1]=include
vpn-policy-routing.@include[1].path='/etc/vpn-policy-routing.aws.user'
vpn-policy-routing.@include[1].enabled='0'
vpn-policy-routing.@policy[0]=policy
vpn-policy-routing.@policy[0].name='Route_VPN_LAN0'
vpn-policy-routing.@policy[0].src_addr='192.168.0.0/24'
vpn-policy-routing.@policy[0].interface='WG_VPN'
Thanks again for the precious help.
Kind Regards,
Lorenzo