Hello,
After some testing, I was able to achieve this configuration. This involves quite a bit of configuration (don't forget to save changes after each step):
- Creating VLANs
- To segregate the traffic from different ports, we will need to create separate VLANs for them. In this configuration, I will be leaving the default LAN interface in place, but it can be disabled if not needed.
- Navigate to Network → VLAN → Port Based;
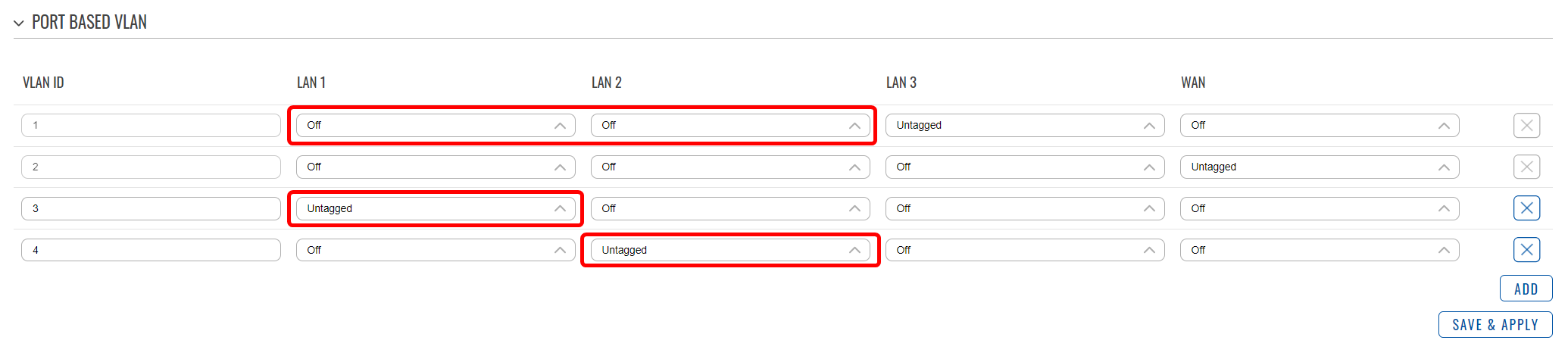
- Add two new VLANs. For this example, I will leave their IDs as 3 and 4;
- Select the LAN1 port as Untagged on VLAN3;
- Select the LAN2 port as Untagged on VLAN4;
- Set the LAN1 and LAN2 ports to Off on VLAN1;
- The table should look like this:
- Creating interfaces
- In this step we will be creating interfaces for the second APN and the new LANs;
- Navigate to Network → Interfaces → General;
- Create a new interface - let's call it lan1;
- Set a static IP in a different subnet from the current LAN network;
- Enable the DHCP server and adjust the options as needed;
- In the Physical Settings tab specify the interface as eth0.3 (VLAN3);
- Create another interface called lan2;
- Set a static IP in a different subnet from the current LAN and lan1 networks;
- Enable the DHCP server and adjust the options as needed;
- In the Physical Settings tab specify the interface as eth0.4 (VLAN4);
- Now that we have created the LAN interfaces, we will need to add an additional interface for the second APN;
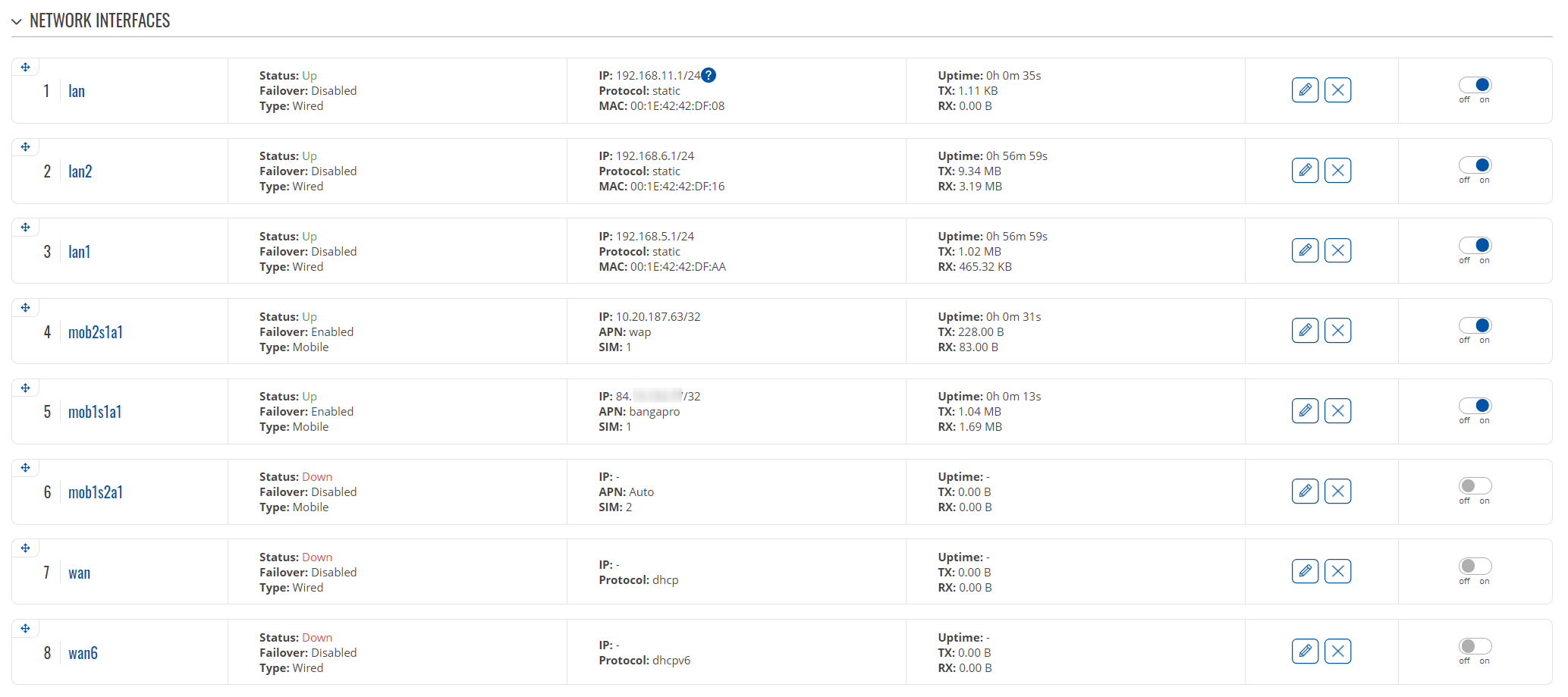
- Add a new interface - I'll call it mob2s1a1, but it can be anything;
- Select the protocol as Mobile;
- Select the same SIM slot as the already active interface uses;
- Specify the APN;
- After saving the settings, it might take some time, but both APNs should be active, and your interface table should look like so (I've disabled the unused interfaces, but feel free to do with them as you wish):
- Firewall configuration
- In this step we will configure the different firewall zones and various settings;
- Navigate to Network → Firewall → General Settings;
- Edit the LAN zone, and from the Covered networks list remove lan1 and lan2 networks;
- Then edit the WAN zone, and from the Covered networks list remove the mobile interfaces;
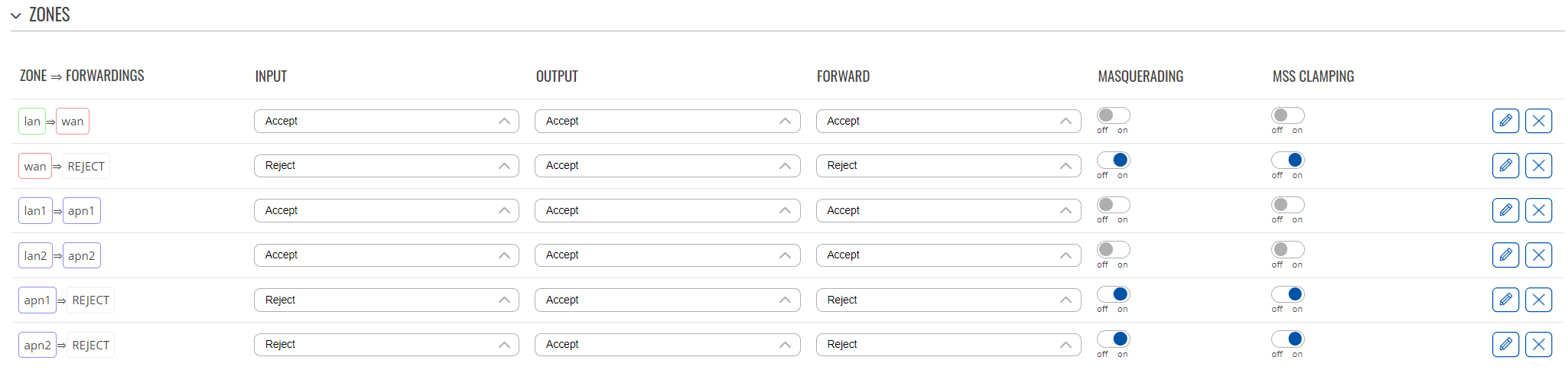
- Create a new zone and rename it to lan1;
- Make sure the Input, Output, and Forward flags are set to Accept;
- In the Covered networks selection add lan1 network;
- Create a new zone and rename it to lan2;
- Make sure the Input, Output, and Forward flags are set to Accept;
- In the Covered networks selection add lan2 network;
- Now that the LAN zones are done, let's create the ones for WAN:
- Create a new zone and rename it to apn1;
- Here, the Input and Forward flags should be set to Reject, while the Output flag should be set to Accept;
- Enable the Masquerading and MSS Clamping;
- Under the covered networks select one of the mobile interfaces;
- In the Allow forward from source zones field add lan1 zone;
- Create a new zone and rename it to apn2;
- The Input and Forward flags should be set to Reject, while the Output flag should be set to Accept;
- Enable the Masquerading and MSS Clamping;
- Under the covered networks select the other active mobile interface;
- In the Allow forward from source zones field add lan2 zone;
- Once that's done, the firewall zone table should look like so:
- Enabling the Load Balancing
- This is needed so that both of the APNs can be used at the same time;
- Navigate to Network → Failover;
- In the top-right corner select the Load balancing option;
- Enable it on the active mobile interfaces with the same ratio;
- Feel free to enable it on any other interfaces you are using.
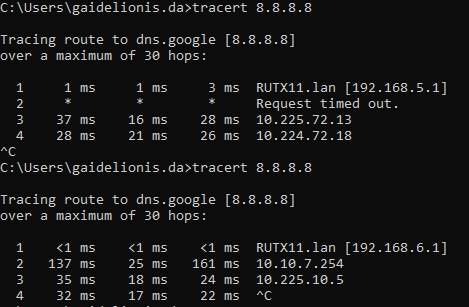
And that's it! I would recommend restarting the router to make sure all of the settings are applied when you plug your PC into the LAN1 port, it should get an IP from the first VLAN, and on the LAN2 port, you should get an IP from the second VLAN. To verify that the traffic is getting routed correctly, use can use tracert command on Windows (traceroute on Linux) and check if the paths taken to the same source differ between the two VLANs:
Let me know if you experience any issues or have any other concerns!
Best regards,
DaumantasG